How to setup OpenVPN server on an ubuntu instance hosted on GCP
Hello! In this article, we’ll guide you through setting up an OpenVPN server on an Ubuntu Linux instance hosted on Google Cloud Platform.
Why Set Up a VPN?
A VPN provides a secure, private connection over public networks, protecting your data and enhancing privacy. It is essential for bypassing geo-restrictions, staying anonymous online, and accessing restricted or censored content.
Configuring Your VM Instance
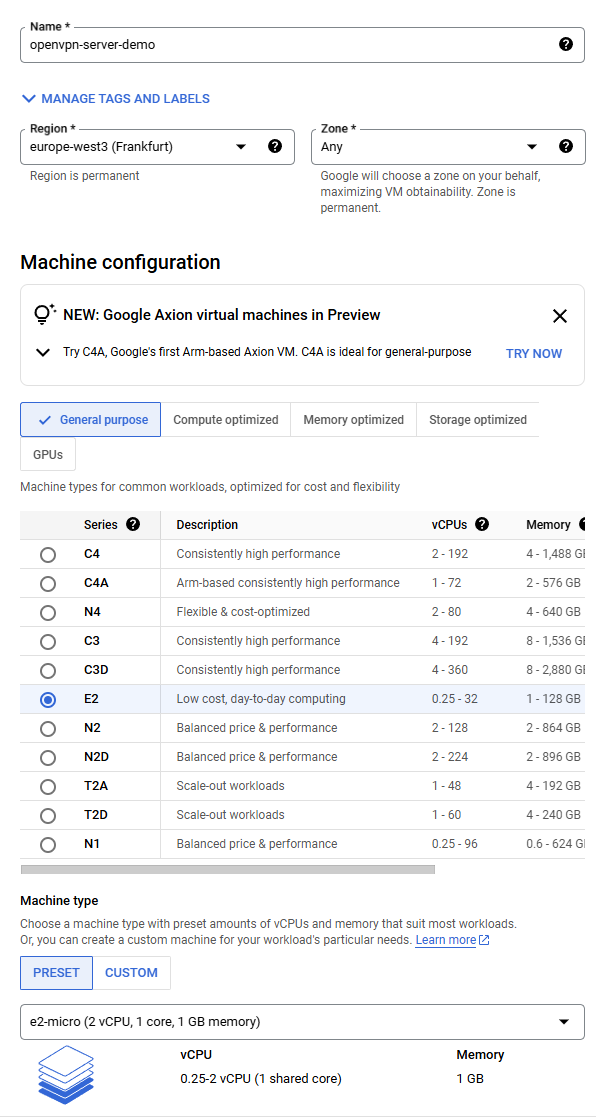
Setting up OpenVPN on your Ubuntu server is straightforward. This guide uses an Ubuntu 24.04 LTS virtual machine on Google Cloud Platform.
- Machine configuration: e2-micro
- Disk: 10GB balanced persistent disk (Ubuntu 24.04 LTS)
- Region: Choose the region nearest you for best performance.
This setup should be sufficient for our OpenVPN server.
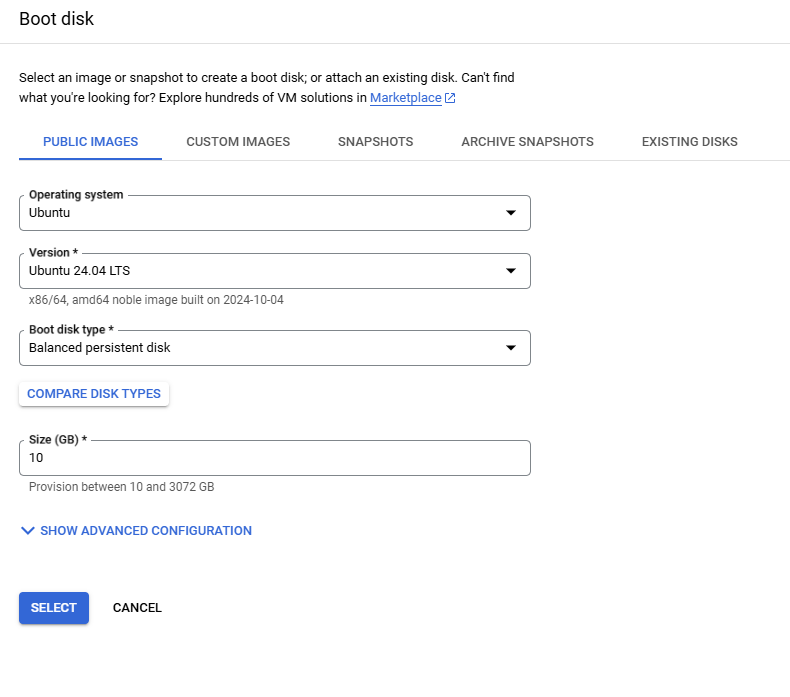
Select the Ubuntu image in the Boot Disk option.
save it.
Setting Up Firewall Rules
In your VPC Network’s firewall settings, allow access to the port OpenVPN will use. Go to Network interfaces under the VM details.
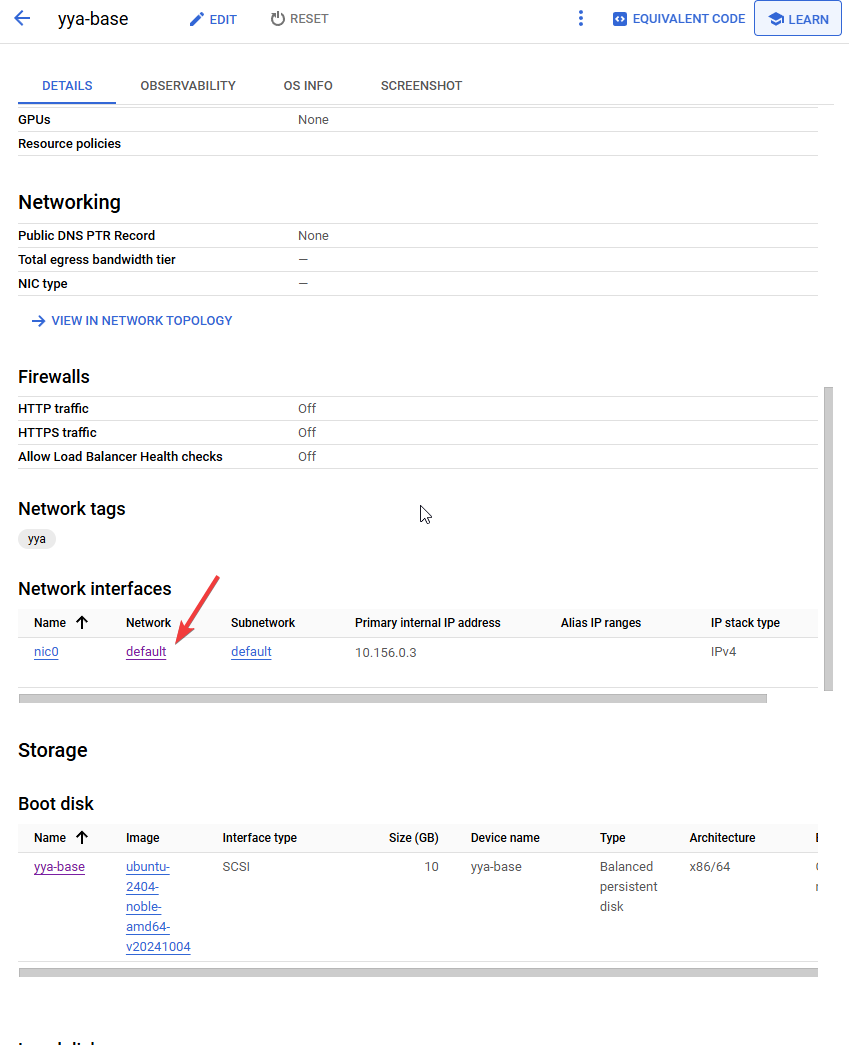
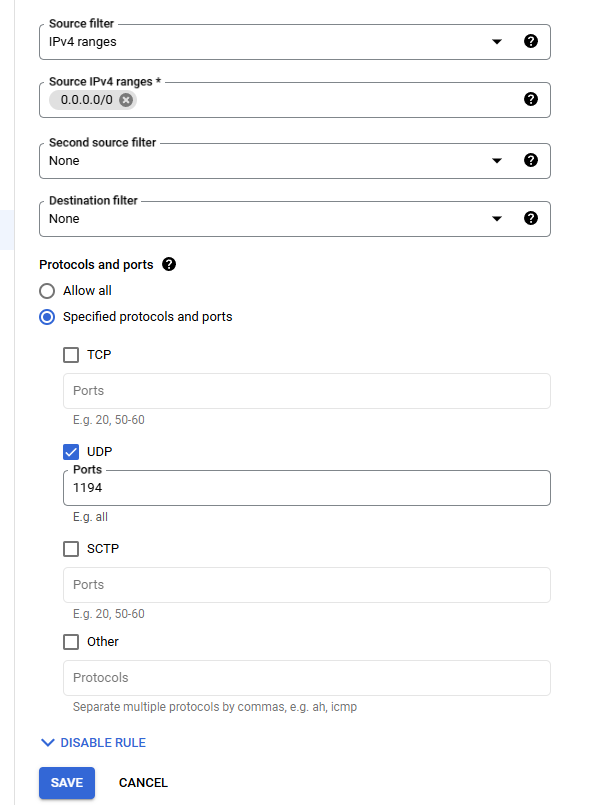
Add a firewall rule for UDP port 1194 (or another port if you prefer).
Installing OpenVPN Server
Connect via SSH and update your packages for security and stability:
sudo apt update
sudo apt upgradeDownload the OpenVPN setup script:
curl -O https://raw.githubusercontent.com/angristan/openvpn-install/master/openvpn-install.shMake the script executable and run it:
chmod +x openvpn-install.sh
sudo ./openvpn-install.shThe assistant will guide you through several setup questions.
Here, it will ask us to confirm the automatically detected IP addresses.
Welcome to the OpenVPN installer!
The git repository is available at: https://github.com/angristan/openvpn-install
I need to ask you a few questions before starting the setup.
You can leave the default options and just press enter if you are ok with them.
I need to know the IPv4 address of the network interface you want OpenVPN listening to.
Unless your server is behind NAT, it should be your public IPv4 address.
IP address: 10.156.0.5Our server’s external IP is displayed here as well. It’s important to use a static IP; otherwise, you will lose access to your vpn every time the server restarts.
It seems this server is behind NAT. What is its public IPv4 address or hostname?
We need it for the clients to connect to the server.
Public IPv4 address or hostname: *******Whether to enable IPv6 – I have it disabled.
Checking for IPv6 connectivity...
Your host does not appear to have IPv6 connectivity.
Do you want to enable IPv6 support (NAT)? [y/n]: nChoosing the port for access: if you plan to use a different port, you can specify it here. I chose the default port 1194 with the UDP protocol. (UDP is faster but has a potential for packet loss.)
What port do you want OpenVPN to listen to?
1) Default: 1194
2) Custom
3) Random [49152-65535]
Port choice [1-3]: 1
What protocol do you want OpenVPN to use?
UDP is faster. Unless it is not available, you shouldn't use TCP.
1) UDP
2) TCP
Protocol [1-2]: 1
For DNS resolver selection, Select Cloudflare (my personal preference) or another option that fits your needs.
What DNS resolvers do you want to use with the VPN?
1) Current system resolvers (from /etc/resolv.conf)
2) Self-hosted DNS Resolver (Unbound)
3) Cloudflare (Anycast: worldwide)
4) Quad9 (Anycast: worldwide)
5) Quad9 uncensored (Anycast: worldwide)
6) FDN (France)
7) DNS.WATCH (Germany)
8) OpenDNS (Anycast: worldwide)
9) Google (Anycast: worldwide)
10) Yandex Basic (Russia)
11) AdGuard DNS (Anycast: worldwide)
12) NextDNS (Anycast: worldwide)
13) Custom
DNS [1-12]: 3
Do you want to use compression? It is not recommended since the VORACLE attack makes use of it.
Enable compression? [y/n]: nAfter the script completes the setup, it will ask us for a client name to create a client profile.
Tell me a name for the client.
The name must consist of alphanumeric character. It may also include an underscore or a dash.
Client name: yyavci-demoYou can optionally password-protect the client configuration file. Here, we use a passwordless setup for simplicity.
Do you want to protect the configuration file with a password?
(e.g. encrypt the private key with a password)
1) Add a passwordless client
2) Use a password for the client
Select an option [1-2]: 1Your client file should now be created in your home directory. Install the OpenVPN client from openvpn-client on your device you’ll use to connect, and import this file.
Creating and Managing Clients
To create or remove clients, or to uninstall OpenVPN, simply rerun the script with:
sudo ./openvpn-install.shReferences
Thank you for following along!